Tenant Management
The Tenant Management grid displays a visual representation of the active tenant for the user’s organization. Admin users can edit tenants by interacting with the Tenant Management Grid.
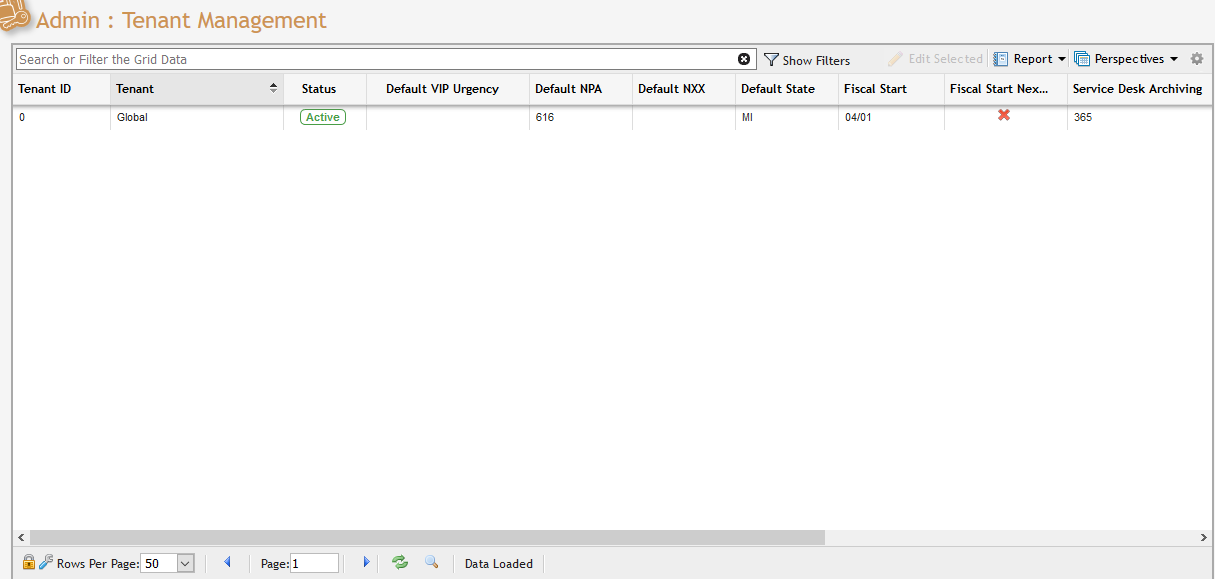
Tenants
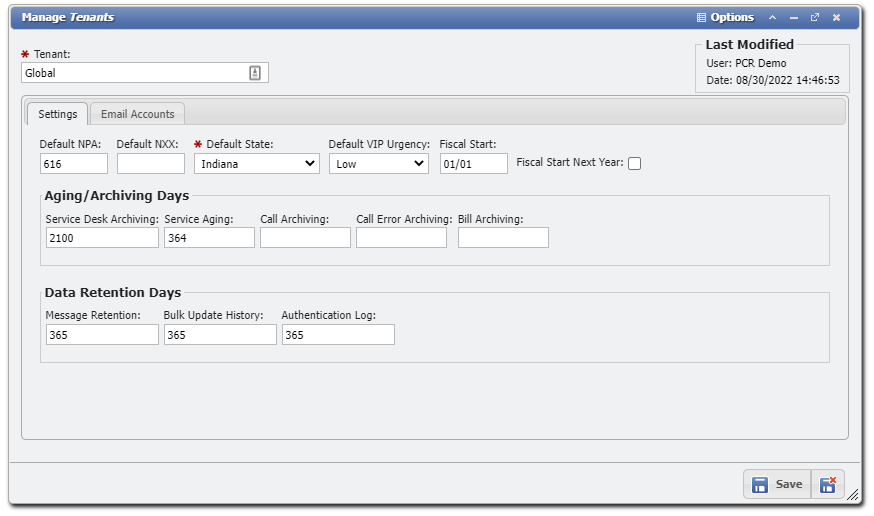
In the Tenant Management data entry form, Admin Users are prompted to define some basic information.
Here, Users can define a Default NPA (a three-digit area code), Default NXX (the first three-digit prefix of a local phone number), and Default State. These values will pre-populate any fields of their respective types in the application.
Users must also apply a VIP Urgency designation to the tenant. If the user defines the VIP Urgency as "High", for example, all SD items owned by VIP users will indicate the elevated need for attention within the Service Desk.
Fiscal Wall
The 'Fiscal Start' field takes a two-digit month/day (MM/DD) to set the start time for an organization's Fiscal Year. This field sets a "Fiscal Wall" that will prevent Charges from being created for any date older than the set Fiscal Year when using Back Billing.
The 'Fiscal Start Next Year' will set the year to the following year if it is set to True. If the checkbox is not set then the current year is used instead.
Aging And Archiving
Several values control how old data is managed within the database.
Aging: Services can be Aged, which allows them to be reused after a particular window of inactive time.
Services: A non-negative (including zero) number of days to leave Inactive Services deactivated before putting them through Service Aging. Zero is respected here, allowing Services to be made available the next time the Aging Event runs. Aging will use the Service's Catalog Aging setting if it has one, otherwise, this value will be used.
Archiving: Some data is Archived by moving old records to cloned tables so current data can continue to perform well. This reduces the load on the database to work with millions of records at a time, most of which are no longer useful on a day-to-day basis.
Calls: A non-negative (including zero) number of days before call data is Archived according to Date/Time the Call occurred. If left empty or 0 is set, 90 will be used instead.
Call Errors: A non-negative (including zero) number of days before Call Error data is Archived. This window can be shorter than typical Call data because it can't be processed for billing. Because the date of the call may fail to import properly, Errors are archived according to the record's Created Date (effectively, Import Date). If left empty or 0 is set, 90 will be used instead.
Bill: A non-negative (including zero) number of days to wait after a Bill is generated to archive its data. This window is based on the date the Bill was generated.
Service Desk: A non-negative (including zero) number of days to wait before Archiving valid Service Desk records. The default value is 365 days. Zero is permitted to Archive Eligible records immediately, though NOT recommended.
Data Retention
PCR-360 is capable of generating large amounts of data. Proper data retention policies and clean up processes will help to keep PCR-360 running as optimal as possible. Retention values apply to the length of time data is preserved before being permanently deleted from the application, whereas Aging is how long Services (or other entities, potentially) retain their current data associations before being "cleaned" for reuse. As a last distinction, Retention and Aging are both separate from Archiving, which defines how long data remains in the "primary" tables.
Data Retention values define how long, in days, the records are kept. Zero indicates records are cleaned up immediately. A negative number is not allowed, but if left blank the event will not clean up any records. Data Retention Events will only clean up the oldest months worth of data per run until the data retention days threshold. This ensures the system is not bogged down when there is a backlog of records. To utilize this event effectively it is recommended to run weekly. Once caught up, it can be changed to monthly, although any performance gains would likely be negligible.
Please contact the helpdesk with questions, or for assistance setting up retention policies.
API Request Logs
The API Request Logs Deleted event recurs daily to cleanup outstanding REST API Request Logs. The number of days the Log is Retained is set on the Manage API Keys form.
Authentication Log
The Authentication Log cleanup event recurs weekly, is set to pending by default, and has a default retention value of 365 days. The retention value is set on the Manage Tenants form.
Bulk Update History
The Bulk Update History cleanup event recurs weekly, is set to pending by default, and has a default retention value of 365 days. The retention value is set on the Manage Tenants form.
Imports
The Delete old Import Files and Imported Records event recurs every day to cleanup records. The retention value for the records is set on the Manage Import File Format form. If the retention value is set too soon it could limit PCR's ability to troubleshoot issues relating to that import format.
Messages
The Messages cleanup event recurs weekly, is set to pending by default, and has a default retention value of 365 days. The retention value for this event is set on the Manage Tenant form. System Messages (BIll generation, Bulk updates, etc.) and Messages of Inactive Users are effected by this event. The PCR-360 messaging system allows Users to send and receive messages from other PCR-360 users, those messages are not deleted by this cleanup event.
Adding Email Accounts
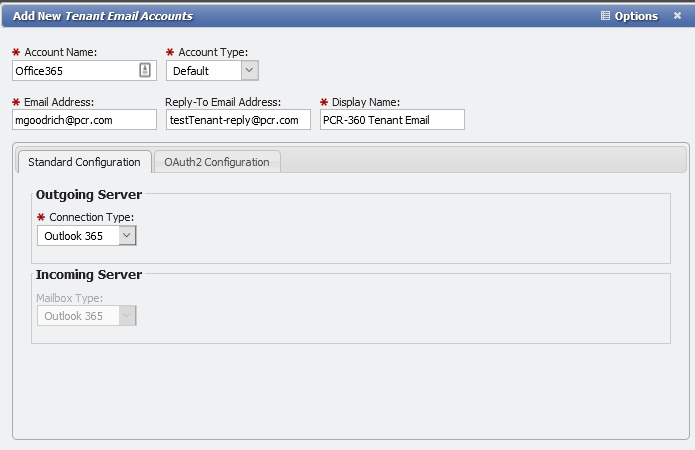
Users can also add email accounts to the tenant. These accounts serve as the "From" and "To" addresses for the automated email capabilities built into the application. Click on the 'Email Accounts' tab and click the 'Add' button (see image above).
In the form (see image above), Admin users are prompted to define a number of required fields for the new email account. This email account specification defines how PCR-360 will send and receive emails. PCR-360 sends email notifications and alerts, and can also "read" incoming emails to a specified email account. For example, if the subject of an incoming email references a specific Service Desk number, the application will add the email to the SD item's Email Thread; if no SD number is specified, the application will create a new Service Desk Inquiry.
Users must define all aspects of the new account, including 'Account Name', 'Account Type', 'Login' and 'Password', the 'Email Address' itself, and the 'Servers' that the account uses.
Setting up the PCR-360 Email
Overview
PCR-360 can be configured to send and receive external Emails from an associated Email address. For information on the compatible Account Types, please see out configuring an Email article.
To set up the initial association:
In the PCR-360 Application, navigate to Admin → Tenant Management.
Select the record in the grid.
Select the Emails Tab
Click the Add button.
PCR-360 is now ready to have a Email Address configured.
Registering An Application in the Portal
Open a browser and navigate to the Azure Active Directory admin center.
Login with an account capable of administrating Active Directory
Select Azure Active Directory in the left-hand navigation, then select App registrations under Manage.

Select New registration. On the Register, an application page, set the values as follows.
Set Name to "PCR360 Production" (or "PCR360 Test" depending on the environment being set up).
Set Supported account types to Accounts in any organizational directory and personal Microsoft accounts.
Under Redirect URI, set the first drop-down to
Weband set the value toThis must be altered to reflect the URL of the PCR-360 Application
Appending /core/oauth2/validated to the end of the URL is required
https://<pcr360.customerUrl.edu>/core/oauth2/validated
Select Register. Copy the value of the Application (client) ID and save it, you will need it later.
Select Certificates & secrets under Manage. Select the New client secret button. Enter a value in Description and select one of the options for Expires and select Add.
Copy the client secret value before you leave this page. You will need it later.
Important
This client secret is never shown again, so make sure you copy it now.

Select API permissions in the side bar
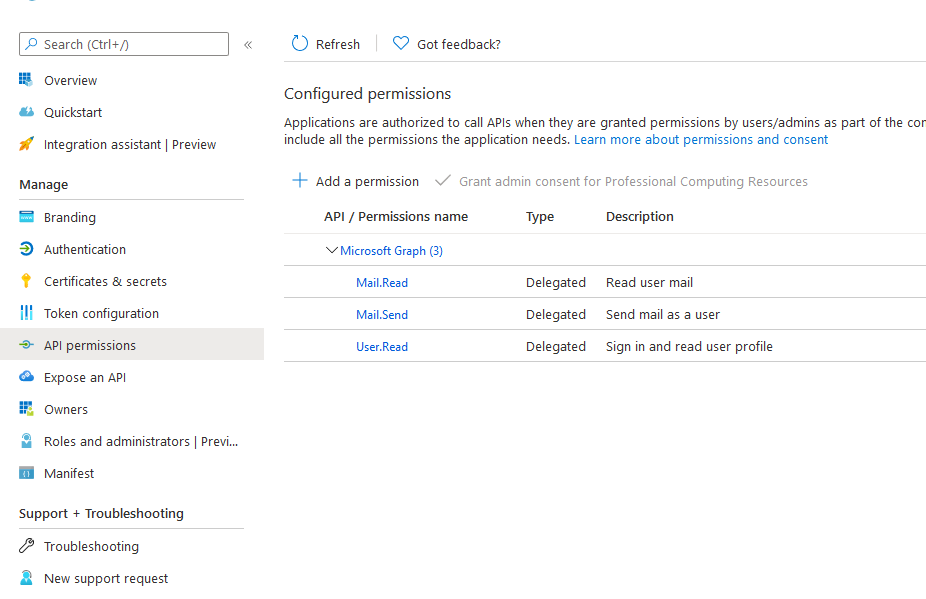
API Permissions Example
Add the permission as shown
Click Add a permission and select Microsoft Graph

Configuration Permissions Example
Select Delegated Permissions
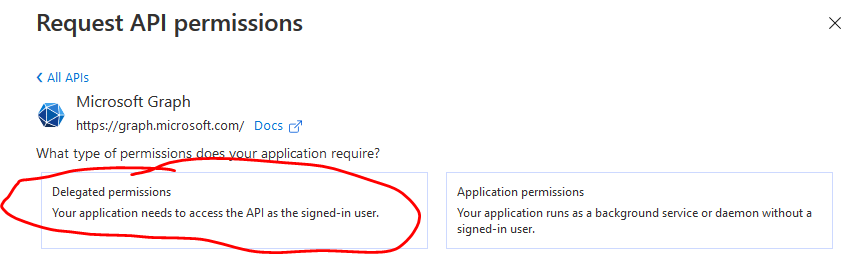
API Permissions example
Select the Mail.Read and Mail.Send permissions
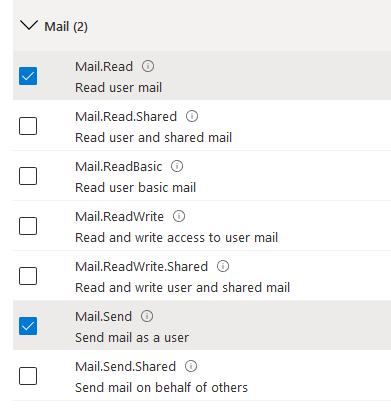
Send Permission example
Select the User.Read permission
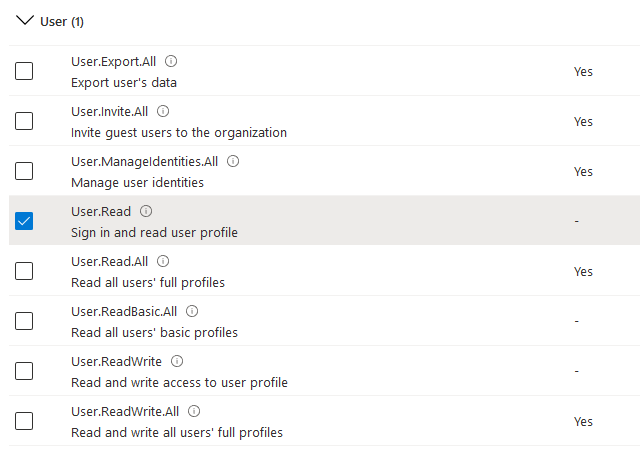
Read Permission example
Click the Add permissions button to add the selected permissions
Add Permissions example
Configuration:
Below is an example for configuring a Microsoft Email to be used by PCR-360
Select the appropriate Account Type.
MAKE SURE TO USE THE EMAIL ADDRESS YOU WANT PCR-360 TO USE
On the OAuth2 Configuration tab enter Application ID and Secret KEY copied down from the Registering an Application steps above.
Also enter in the following values:
Authentication Authority URL: https://login.microsoftonline.com/common for this example
Authorization Endpoint: /oauth2/v2.0/authorize
Token Request Endpoint: /oauth2/v2.0/token
Scopes (groups, or permissions): openid profile offline_access user.read mail.read mail.send
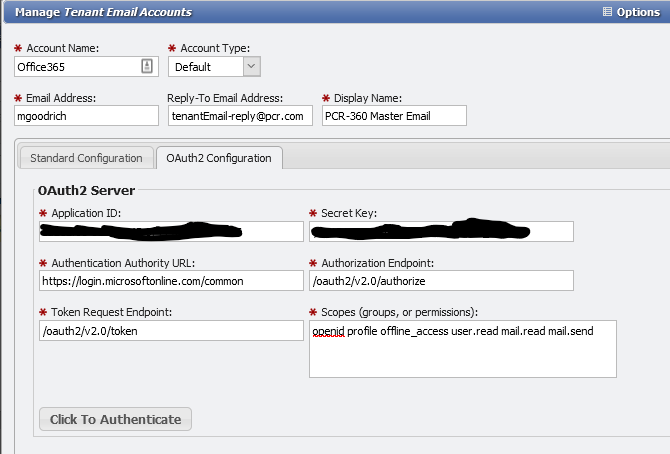
Manage Tenant Email Example
Save the Email Address
Click the "Click to Authenticate" button
Follow the prompts to authorize PCR-360 with your Email.
Once completed the portal will redirect back to the application with a success message.
The button on the OAuth2 Configuration tab should now say "Click to RE Authenticate"
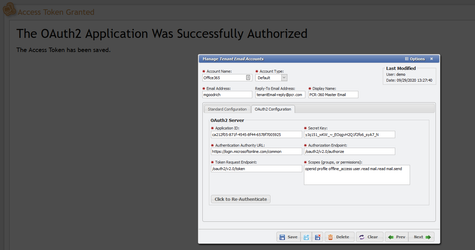
The application is now configured to send (and/or receive) emails using the email address that was authenticated
